Information Security
Kioxia Group treats information as a critical asset and is committed to eliminating and reducing information security risks in our business activities in order to protect and utilize this valuable resource.
Information Security Management
Information Security Management Policy
The utilization of data and cloud services and the use of AI have increased in line with digital transformation, and we are also seeing more diverse working styles, such as a rise in telecommuting. With cyber-attacks becoming increasingly sophisticated and able to cause more serious damage to companies' businesses, cyber security measures have become more important each year.
Information security is a key management issue for Kioxia Group, and we recognize the sensitivity and value of all information handled during the course of our business activities, including personal information, customer and business partner information, management information, and technical and production information. Our basic policy is to manage such information in a confidential manner in order to protect it and prevent inappropriate disclosures, leaks or improper use. Furthermore, we are taking steps to enhance the reliability of our operations by obtaining, and through the activities to obtain, the information security certifications necessary for our business activities.
Structure of Information Security Management
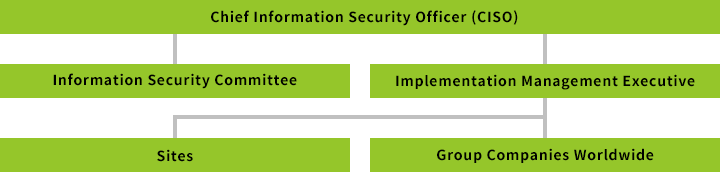
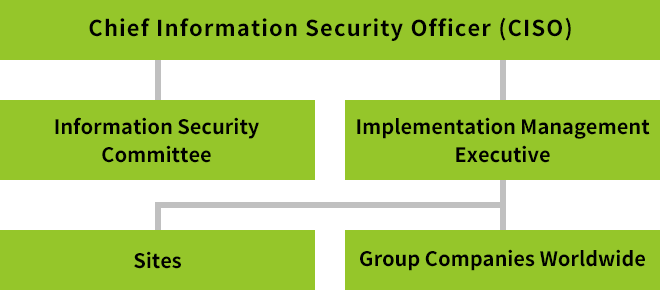
Kioxia Group has assigned its Executive of Information Security as the Chief Information Security Officer (CISO), whose responsibility is to oversee and ensure compliance with our Information Security Management Policy across the Group. We have also assigned responsibility for managing and implementing our information security measures to the General Manager of our Cyber Security Center. Information security management processes incorporating the protection of personal information have been implemented at each business site and organization at all Group companies. The Information Security Committee deliberates matters that are deemed key to ensuring information security throughout the Group.
In addition, the implementation status of relevant measures and specific issues arising in any of our Group companies are reported to our executive officers on a regular basis in order to standardize and improve the level of information security throughout Kioxia Group.
Kioxia Group’s Information Security Management Structure
Information Security Measures
In FY2024, Kioxia Group implemented information security measures that included the reinforcement of networks and internal system monitoring from four perspectives.
Implementation of Information Security Measures
|
Category |
Description |
|---|---|
|
(1) Organizational measures: |
|
|
(2) Human resource and legal measures: |
|
|
(3) Physical measures: |
|
|
(4) Technical measures: |
|
|
(5) Other measures |
Promotion of information security enhancement in cooperation with national governments and related ministries and agencies, and incorporation of industry-wide best practices |
Education, Inspection and Audit of Information Security Management
All Kioxia Group’s divisions and organizations conduct annual self-inspections and self-audits of their compliance with information security policies and internal rules. They identify any issues and seek to address these in an effort to improve the level of information security within each of them.
Kioxia Group conducts annual training for all officers and employees and management communicates relevant messages regarding information security to all employees in order to ensure strict compliance with all in-house regulations.
Responding to Incidents such as Leakage of Confidential Information
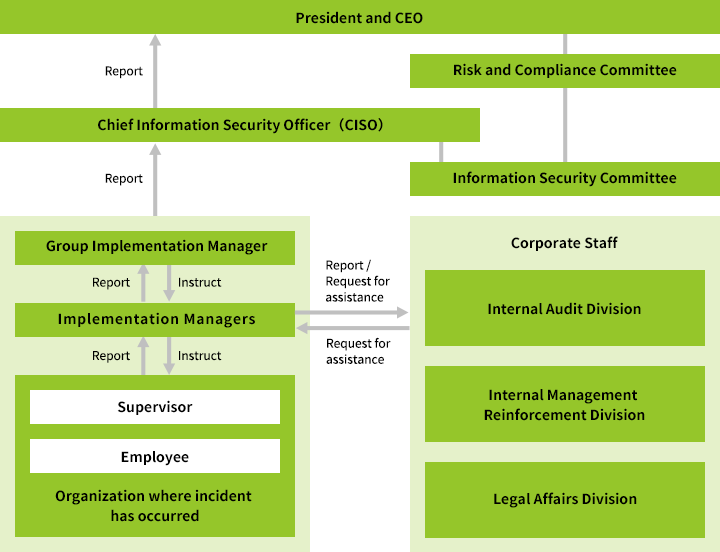
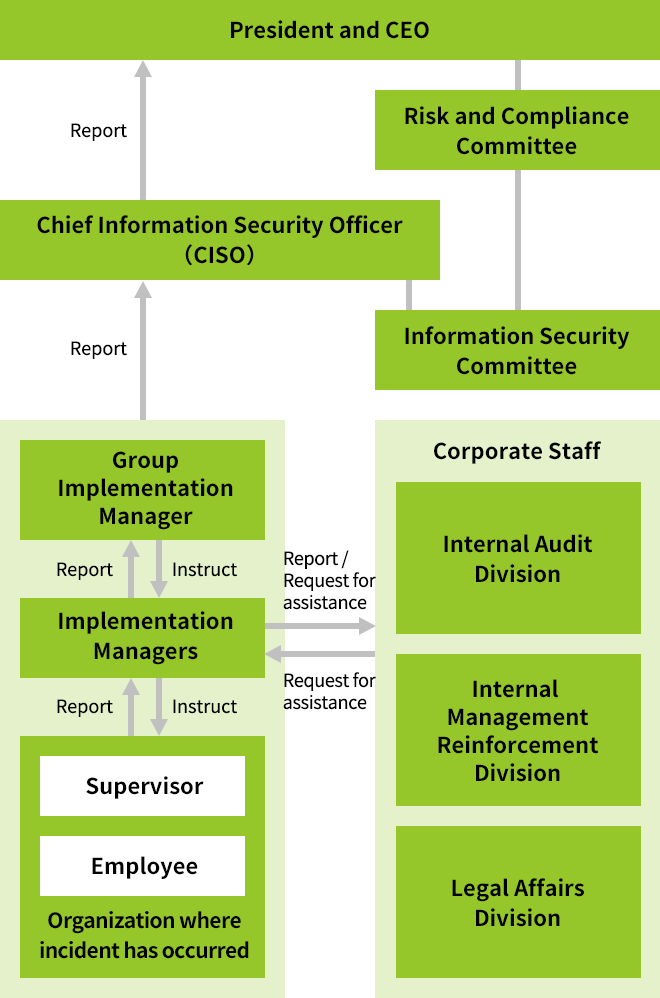
In the event an information security incident such as a leakage of confidential information occurs, Kioxia Group responds promptly in accordance with its information security incident reporting processes.
When we become aware of the occurrence or potential occurrence of an incident involving a serious leakage of confidential information that may entail a violation of any laws or ordinances, we strive to respond promptly based on our risk and compliance management processes.
Kioxia Group's Information Security Incident Reporting Process
Status of Incidents such as Leakage of Confidential Information
In FY2024, there were no incidents of sensitive information held by Kioxia Group companies being leaked, nor were there any complaints from relevant external individuals or regulatory bodies concerning personal information. We will continue to work to prevent information security incidents and ensure we are fully prepared for any situation that might arise.
Product Security Management
Product Security Management Policy
Kioxia Group responds promptly to any cyber-security risks emerging in society at large, and to requests from customers and other stakeholders related to product security.
Kioxia Group defines “Product Security” as the prevention of any malicious information leaks, falsification, or unforeseeable faults in the products and services we sell or provide to our customers. Our basic policy is to establish a product security management framework that ensures the provision of secure and safe products and aims to minimize any cyber-security risks associated with them.
We have drawn up this basic product security policy and we ensure all employees and officers of the Group are fully aware of it.
Structure of Product Security Management
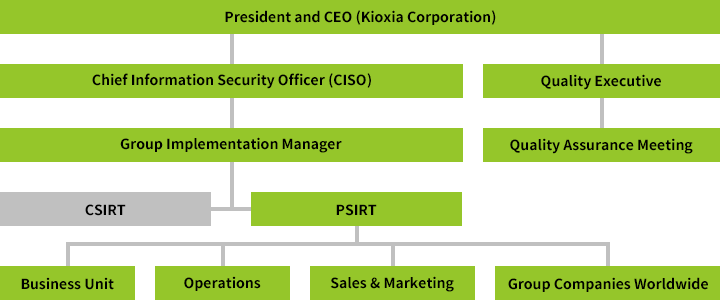
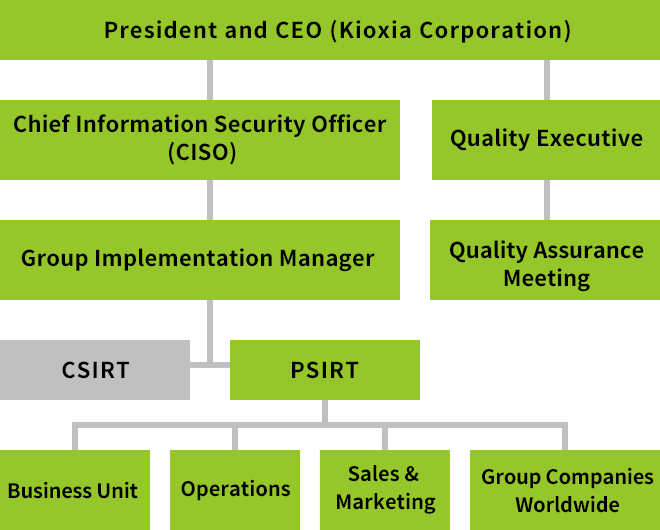
Kioxia Group has appointed a Chief Information Security Officer at Kioxia Corporation whose responsibilities include ensuring compliance with our Product Security Policy across the Group. In each business division we have formulated product security management processes that are strongly integrated with our quality management system. We have also established a special support service we call the Product Security Incident Response Team (PSIRT)¹ which enables us to respond promptly to inquiries and to address any security vulnerabilities in our products. In addition, we have established processes governing the operation of the Computer Security Incident Response Team (CSIRT),² which responds to incidents and inquiries about information assets.
- 1 A team that responds to product security issues
- 2 A team that addresses information security issues
Kioxia Group's Product Security Management Structure
Product Security Measures
In addition to the aforementioned organizational, process and legal measures, the following internal rules and regulations have been established to implement security measures for our products.
|
Category |
Description |
|---|---|
|
(1) Legal and regulatory compliance |
|
|
(2) Secure development: establishing processes to ensure we provide secure products |
|
|
(3) Incident system development: dealing with product vulnerabilities, inquiries, etc. |
|
Response to Product-Related Security Incidents
In the event of a security incident caused by a cyber-attack, for example one targeting product vulnerabilities, Kioxia Group will strive to respond promptly, with PSIRT and the Group implementation manager assessing the situation based on our product security management processes and on our formulated responses to product incidents.
Status of any Product Vulnerabilities and Our Responses
There were no serious incidents associated with vulnerabilities in any of our products in FY2024. We will continue to strive to prevent the risk of product vulnerabilities, and we will ensure swift detection and a prompt response to any that are found.